Which of the Following Best Describes the Threat Modelling Process

A Step By Step Roadmap That Describes The Synergy And Context Between Business And It Information Governance Operating Model Technology Roadmap

Application Landscape 2011 Landscape Diagram Schematic Design Free Landscape Design

Porter S Generic Strategies Porter S Generic Strategies Leadership Strategies Strategies
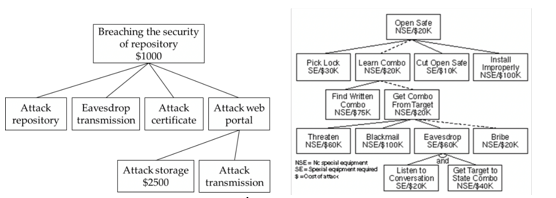
Threat Modeling 12 Available Methods

Arrow Process Diagram Template For Powerpoint And Keynote Process Infographic Diagram Design Powerpoint

Threat Modeling 12 Available Methods

Practice Of Raci Matrix In An Organization Bba Lectures Leadership Management Critical Thinking Skills Human Resources Career

The Ultimate Guide To Email Security Best Practices For Employees To Protect Your Organization Emailsecurity Email Security Security Solutions Cyber Security

Revenue Cycle Management Revenue Cycle Revenue Cycle Management Revenue Management

Model Of The Elements Of Strategic Management Process Chart Strategic Planning Strategic

Wikimedia Commons Has Media Related To Diagrams Flow Chart Data Flow Diagram Decision Making

Cybersecurity Reference Architecture Security For A Hybrid Enterprise Microsoft Security Blog Enterprise Architecture Security Architecture Cyber Security
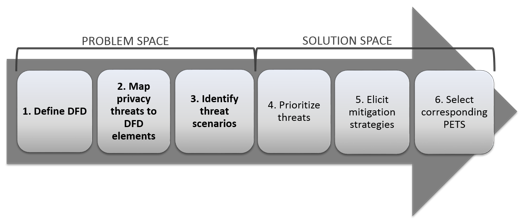
Threat Modeling 12 Available Methods

Abrsm Music Theory Grade 5 2014 A Book Sites Grade 1 Music Theory

Threat Modeling 12 Available Methods

Diablo 3 The Perfected Monk By Mansarali Deviantart Com On Deviantart Monk Dnd Character Portraits Monk

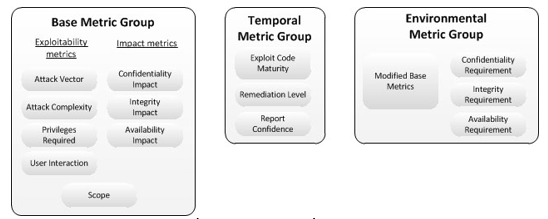
Threat Modeling 12 Available Methods

Kaios Feature Phone Business Model And Why It Matters So Much Fourweekmba Vertical Integration Business Strategy Online Marketing Services

The Reliable Proxy Service For Best Secure Server Local Proxies Computer Security Cyber Security Best Computer

Comments
Post a Comment